Quick and Dirty
Neste post, vou falar sobre como fazer a instalação do WebGoat 5.4 no Ubuntu Server 13.04 – Daily 18-12-2012. Para isso é necessário fazer download do snapshot night do Ubuntu, no caso do dia deste post é Ubuntu Server 13.04 – Daily 18-12-2012:
1. Fazer download a ISO:
2. Criar VM:
Feito o download, crie uma VM no VirtualBox, com as seguintes configurações:
- UD1304_WebGoat (nome da VM)
- 512Mb RAM
- HD 10Gb
3. Atualizar pacotes na VM:
apt-get update -y
apt-get upgrade -y
OBS: Não instalar tomcat do Ubuntu 13.04. Será usado do próprio WebGoat
4.Instalar X-windows e interface gráfica:
apt-get install openbox xorg firefox -y
5.Iniciar interface gráfica:
startx
6. Habilitar recursos Guest na VM via Virtualbox:
No VirtualBox habilitar:
Devices->Install Guest Additions
7. Instalar/Habilitar recursos Guest na VM via Virtualbox no ubuntu 13.04:
sudo mount /dev/dvd /mnt
sh /mnt/VBoxLinuxAdditions.sun
init 6
8. Esses pacotes devem estar instalados na VM para usar o WebGoat com X-Windows corretamente:
accountsservice
acl
acpid
adduser
apparmor
apport
apport-symptoms
apt
apt-transport-https
apt-utils
apt-xapian-index
aptdaemon
aptitude
aptitude-common
aspell
aspell-en
at
at-spi2-core
base-files
base-passwd
bash
bash-completion
bc
bind9-host
binutils
biosdevname
bsdmainutils
bsdutils
busybox-initramfs
busybox-static
byobu
bzip2
ca-certificates
colord
command-not-found
command-not-found-data
console-setup
consolekit
coreutils
cpio
cpp
cpp-4.7
crash
crda
cron
curl
dash
dbus
dbus-x11
dconf-gsettings-backend:amd64
dconf-service
debconf
debconf-i18n
debianutils
dictionaries-common
diffstat
diffutils
dmidecode
dmsetup
dnsutils
docbook-xml
dosfstools
dpkg
e2fslibs:amd64
e2fsprogs
ed
eject
enchant
ethtool
file
findutils
firefox
firefox-globalmenu
fontconfig
fontconfig-config
fonts-ubuntu-font-family-console
friendly-recovery
ftp
fuse
gcc
gcc-4.7
gcc-4.7-base:amd64
gconf-service
gconf-service-backend
gconf2
gconf2-common
gedit
gedit-common
geoip-database
gettext
gettext-base
gir1.2-atk-1.0
gir1.2-freedesktop
gir1.2-gdkpixbuf-2.0
gir1.2-glib-2.0
gir1.2-gtk-3.0
gir1.2-gtksource-3.0
gir1.2-pango-1.0
gir1.2-peas-1.0
glib-networking:amd64
glib-networking-common
glib-networking-services
gnome-user-guide
gnupg
gpgv
grep
groff-base
grub-common
grub-gfxpayload-lists
grub-pc
grub-pc-bin
grub2-common
gsettings-desktop-schemas
gsfonts
gsfonts-x11
gvfs:amd64
gvfs-common
gvfs-daemons
gvfs-libs:amd64
gzip
hardening-includes
hdparm
hicolor-icon-theme
hostname
hunspell-en-us
ifupdown
info
initramfs-tools
initramfs-tools-bin
initscripts
insserv
install-info
installation-report
intltool-debian
iproute
iptables
iputils-ping
iputils-tracepath
irqbalance
isc-dhcp-client
isc-dhcp-common
iso-codes
java-common
kbd
kexec-tools
keyboard-configuration
klibc-utils
kmod
krb5-locales
landscape-common
language-pack-en
language-pack-en-base
language-selector-common
laptop-detect
less
libaccountsservice0
libacl1:amd64
libapt-inst1.5:amd64
libapt-pkg-perl
libapt-pkg4.12:amd64
libarchive-zip-perl
libart-2.0-2:amd64
libasn1-8-heimdal:amd64
libasound2:amd64
libaspell15
libasprintf-dev:amd64
libasprintf0c2:amd64
libatasmart4:amd64
libatk-bridge2.0-0:amd64
libatk1.0-0:amd64
libatk1.0-data
libatspi2.0-0:amd64
libattr1:amd64
libavahi-client3:amd64
libavahi-common-data:amd64
libavahi-common3:amd64
libavahi-glib1:amd64
libbind9-80
libblkid1:amd64
libbonobo2-0:amd64
libbonobo2-common
libbonoboui2-0:amd64
libbonoboui2-common
libboost-iostreams1.49.0
libbsd0:amd64
libbz2-1.0:amd64
libc-bin
libc-dev-bin
libc6:amd64
libc6-dev:amd64
libcairo-gobject2:amd64
libcairo-perl
libcairo2:amd64
libcanberra-gtk3-0:amd64
libcanberra-gtk3-module:amd64
libcanberra0:amd64
libcap-ng0
libcap2:amd64
libck-connector0:amd64
libclass-accessor-perl
libclass-isa-perl
libclone-perl
libcolord1:amd64
libcomerr2:amd64
libcroco3:amd64
libcups2:amd64
libcurl3:amd64
libcurl3-gnutls:amd64
libcwidget3
libdatrie1:amd64
libdb5.1:amd64
libdbus-1-3:amd64
libdbus-glib-1-2:amd64
libdbusmenu-glib4:amd64
libdbusmenu-gtk4:amd64
libdconf1:amd64
libdee-1.0-4
libdevmapper1.02.1:amd64
libdigest-hmac-perl
libdns88
libdpkg-perl
libdrm-intel1:amd64
libdrm-nouveau2:amd64
libdrm-radeon1:amd64
libdrm2:amd64
libdw1:amd64
libedit2:amd64
libelf1:amd64
libemail-valid-perl
libenchant1c2a
libept1.4.12
libevent-2.0-5:amd64
libexif12:amd64
libexpat1:amd64
libffi6:amd64
libfile-basedir-perl
libfile-desktopentry-perl
libfile-fcntllock-perl
libfile-mimeinfo-perl
libfontconfig1:amd64
libfontenc1:amd64
libfreetype6:amd64
libfribidi0:amd64
libfs6:amd64
libfuse2:amd64
libgail-3-0:amd64
libgail18:amd64
libgc1c2
libgcc-4.7-dev:amd64
libgcc1:amd64
libgconf-2-4:amd64
libgcrypt11:amd64
libgd2-xpm:amd64
libgdbm3:amd64
libgdk-pixbuf2.0-0:amd64
libgdk-pixbuf2.0-common
libgeoclue0
libgeoip1:amd64
libgettextpo-dev:amd64
libgettextpo0:amd64
libgif4:amd64
libgirepository-1.0-1
libgl1-mesa-dri:amd64
libgl1-mesa-glx:amd64
libglade2-0:amd64
libglapi-mesa:amd64
libglib-perl
libglib2.0-0:amd64
libglu1-mesa:amd64
libgmp10:amd64
libgnome-keyring-common
libgnome-keyring0:amd64
libgnome2-0:amd64
libgnome2-bin
libgnome2-common
libgnomecanvas2-0:amd64
libgnomecanvas2-common
libgnomeui-0:amd64
libgnomeui-common
libgnomevfs2-0:amd64
libgnomevfs2-common
libgnutls26:amd64
libgomp1:amd64
libgpg-error0:amd64
libgphoto2-2:amd64
libgphoto2-l10n
libgphoto2-port0:amd64
libgpm2:amd64
libgssapi-krb5-2:amd64
libgssapi3-heimdal:amd64
libgstreamer-plugins-base1.0-0:amd64
libgstreamer1.0-0:amd64
libgtk-3-0:amd64
libgtk-3-bin
libgtk-3-common
libgtk2-perl
libgtk2.0-0:amd64
libgtk2.0-bin
libgtk2.0-common
libgtksourceview-3.0-0:amd64
libgtksourceview-3.0-common
libgudev-1.0-0:amd64
libgusb2
libhcrypto4-heimdal:amd64
libheimbase1-heimdal:amd64
libheimntlm0-heimdal:amd64
libhunspell-1.3-0:amd64
libhx509-5-heimdal:amd64
libice6:amd64
libicu48:amd64
libid3tag0
libidl-common
libidl0:amd64
libidn11:amd64
libieee1284-3:amd64
libimlib2
libio-pty-perl
libio-socket-inet6-perl
libio-string-perl
libipc-run-perl
libisc84
libisccc80
libisccfg82
libitm1:amd64
libiw30:amd64
libjasper1:amd64
libjavascriptcoregtk-3.0-0
libjbig0:amd64
libjpeg-turbo8:amd64
libjpeg8:amd64
libjson-glib-1.0-0:amd64
libjson0:amd64
libk5crypto3:amd64
libkeybinder0
libkeyutils1:amd64
libklibc
libkmod2:amd64
libkrb5-26-heimdal:amd64
libkrb5-3:amd64
libkrb5support0:amd64
liblcms2-2:amd64
libldap-2.4-2:amd64
libllvm3.1:amd64
liblocale-gettext-perl
liblockfile-bin
liblockfile1:amd64
libltdl7:amd64
liblwres80
liblzma5:amd64
libmagic1:amd64
libmailtools-perl
libmount1:amd64
libmpc2:amd64
libmpfr4:amd64
libmtdev1:amd64
libncurses5:amd64
libncursesw5:amd64
libnet-dns-perl
libnet-domain-tld-perl
libnet-ip-perl
libnewt0.52
libnfnetlink0
libnih-dbus1:amd64
libnih1:amd64
libnl-3-200:amd64
libnl-genl-3-200:amd64
libnotify4:amd64
libnuma1
libobrender27
libobt0
libogg0:amd64
liborbit2:amd64
liborc-0.4-0:amd64
libp11-kit0:amd64
libpam-ck-connector:amd64
libpam-modules:amd64
libpam-modules-bin
libpam-runtime
libpam0g:amd64
libpango-perl
libpango1.0-0:amd64
libparse-debianchangelog-perl
libparted0debian1:amd64
libpcap0.8:amd64
libpci3:amd64
libpciaccess0:amd64
libpcre3:amd64
libpcsclite1:amd64
libpeas-1.0-0
libpeas-common
libpipeline1:amd64
libpixman-1-0:amd64
libplymouth2:amd64
libpng12-0:amd64
libpolkit-agent-1-0:amd64
libpolkit-backend-1-0:amd64
libpolkit-gobject-1-0:amd64
libpopt0:amd64
libprocps0:amd64
libproxy1:amd64
libpython2.7:amd64
libpython2.7-minimal:amd64
libpython2.7-stdlib:amd64
libpython3.3:amd64
libpython3.3-minimal:amd64
libpython3.3-stdlib:amd64
libquadmath0:amd64
librarian0
libreadline5:amd64
libreadline6:amd64
libroken18-heimdal:amd64
librtmp0:amd64
libsane:amd64
libsane-common
libsasl2-2:amd64
libsasl2-modules:amd64
libsecret-1-0:amd64
libsecret-common
libselinux1:amd64
libsigc++-2.0-0c2a:amd64
libslang2:amd64
libsm6:amd64
libsocket6-perl
libsoup2.4-1:amd64
libsqlite3-0:amd64
libss2:amd64
libssl1.0.0:amd64
libstartup-notification0:amd64
libstdc++6:amd64
libsub-name-perl
libswitch-perl
libtasn1-3:amd64
libtdb1:amd64
libtelepathy-glib0:amd64
libtext-charwidth-perl
libtext-iconv-perl
libtext-wrapi18n-perl
libthai-data
libthai0:amd64
libtiff5:amd64
libtimedate-perl
libtinfo5:amd64
libtxc-dxtn-s2tc0:amd64
libudev0:amd64
libudisks2-0:amd64
libunistring0:amd64
libunwind8
liburi-perl
libusb-0.1-4:amd64
libusb-1.0-0:amd64
libutempter0
libuuid1:amd64
libv4l-0:amd64
libv4lconvert0:amd64
libvorbis0a:amd64
libvorbisfile3:amd64
libvte-2.90-9
libvte-2.90-common
libvte-common
libvte9
libwebkitgtk-3.0-0
libwebkitgtk-3.0-common
libwhoopsie0
libwind0-heimdal:amd64
libx11-6:amd64
libx11-data
libx11-xcb1:amd64
libxapian22
libxatracker1:amd64
libxau6:amd64
libxaw7:amd64
libxcb-dri2-0:amd64
libxcb-glx0:amd64
libxcb-render0:amd64
libxcb-shape0:amd64
libxcb-shm0:amd64
libxcb-util0:amd64
libxcb1:amd64
libxcomposite1:amd64
libxcursor1:amd64
libxdamage1:amd64
libxdmcp6:amd64
libxext6:amd64
libxfixes3:amd64
libxfont1
libxft2:amd64
libxi6:amd64
libxinerama1:amd64
libxkbfile1:amd64
libxml2:amd64
libxmu6:amd64
libxmuu1:amd64
libxpm4:amd64
libxrandr2:amd64
libxrender1:amd64
libxslt1.1:amd64
libxt6:amd64
libxtst6:amd64
libxv1:amd64
libxvmc1
libxxf86dga1:amd64
libxxf86vm1:amd64
libyelp0
libzeitgeist-1.0-1
lintian
linux
linux-crashdump
linux-doc
linux-firmware
linux-generic
linux-headers-3.7.0-6
linux-headers-3.7.0-6-generic
linux-headers-3.7.0-7
linux-headers-3.7.0-7-generic
linux-headers-generic
linux-image-3.7.0-6-generic
linux-image-3.7.0-7-generic
linux-image-extra-3.7.0-6-generic
linux-image-extra-3.7.0-7-generic
linux-image-generic
linux-libc-dev:amd64
linux-source
linux-source-3.7.0
linux-tools
linux-tools-3.7.0-7
linux-tools-common
locales
lockfile-progs
login
logrotate
lsb-base
lsb-release
lshw
lsof
ltrace
make
makedev
makedumpfile
man-db
manpages
manpages-dev
mawk
memtest86+
mime-support
mlocate
module-init-tools
mount
mountall
mtr-tiny
multiarch-support
nano
ncurses-base
ncurses-bin
net-tools
netbase
netcat-openbsd
notification-daemon
ntfs-3g
ntpdate
obconf
openbox
openbox-themes
openssh-client
openssl
oracle-java7-installer
oracle-jdk7-installer
os-prober
parted
passwd
patch
patchutils
pciutils
perl
perl-base
perl-modules
plymouth
plymouth-theme-ubuntu-text
policykit-1
policykit-1-gnome
popularity-contest
powermgmt-base
ppp
pppconfig
pppoeconf
procps
psmisc
python
python-apt
python-apt-common
python-cairo
python-chardet
python-dbus
python-dbus-dev
python-debian
python-gconf
python-gdbm
python-gi
python-gi-cairo
python-gnome2
python-gobject
python-gobject-2
python-gtk2
python-keybinder
python-minimal
python-newt
python-notify
python-openssl
python-pam
python-pkg-resources
python-pyorbit
python-serial
python-six
python-twisted-bin
python-twisted-core
python-vte
python-xapian
python-xdg
python-zeitgeist
python-zope.interface
python2.7
python2.7-minimal
python3
python3-apport
python3-apt
python3-aptdaemon
python3-dbus
python3-defer
python3-distupgrade
python3-gdbm
python3-gi
python3-minimal
python3-pkg-resources
python3-problem-report
python3-software-properties
python3-update-manager
python3.3
python3.3-minimal
rarian-compat
readline-common
resolvconf
rsync
rsyslog
screen
sed
sensible-utils
sgml-base
sgml-data
shared-mime-info
software-properties-common
sound-theme-freedesktop
strace
sudo
synaptic
sysv-rc
sysvinit-utils
tar
tasksel
tasksel-data
tcpdump
telnet
terminator
time
tmux
ttf-dejavu-core
tzdata
ubuntu-keyring
ubuntu-minimal
ubuntu-release-upgrader-core
ubuntu-standard
ucf
udev
udisks2
ufw
unattended-upgrades
unzip
update-manager-core
update-notifier-common
upstart
ureadahead
usbutils
util-linux
uuid-runtime
vim
vim-common
vim-runtime
vim-tiny
w3m
wget
whiptail
whoopsie
wireless-regdb
wireless-tools
wpasupplicant
x11-apps
x11-common
x11-session-utils
x11-utils
x11-xfs-utils
x11-xkb-utils
x11-xserver-utils
xauth
xbitmaps
xdg-utils
xfonts-base
xfonts-encodings
xfonts-scalable
xfonts-utils
xinit
xinput
xkb-data
xml-core
xorg
xorg-docs-core
xserver-common
xserver-xorg
xserver-xorg-core
xserver-xorg-input-all
xserver-xorg-input-evdev
xserver-xorg-input-mouse
xserver-xorg-input-synaptics
xserver-xorg-input-vmmouse
xserver-xorg-input-wacom
xserver-xorg-video-all
xserver-xorg-video-ati
xserver-xorg-video-cirrus
xserver-xorg-video-fbdev
xserver-xorg-video-intel
xserver-xorg-video-mach64
xserver-xorg-video-mga
xserver-xorg-video-modesetting
xserver-xorg-video-neomagic
xserver-xorg-video-nouveau
xserver-xorg-video-openchrome
xserver-xorg-video-qxl
xserver-xorg-video-r128
xserver-xorg-video-radeon
xserver-xorg-video-s3
xserver-xorg-video-savage
xserver-xorg-video-siliconmotion
xserver-xorg-video-sis
xserver-xorg-video-sisusb
xserver-xorg-video-tdfx
xserver-xorg-video-trident
xserver-xorg-video-vesa
xserver-xorg-video-vmware
xterm
xul-ext-ubufox
xz-utils
yelp
yelp-xsl
zeitgeist
zeitgeist-core
zeitgeist-datahub
zenity
zenity-common
zlib1g:amd64
10. Novamente
sudo mount /dev/dvd /mnt
sh /mnt/VBoxLinuxAdditions.sun
init 6
11. Para habilitar Copiar/Colar e Arrastar/Soltar no VirtualBox:
Nos menus do VirtualBox:
Devices->Share Clipboard->Bidirectional
Devices->Drag ‘n’ Drog->Bidirectional
View->Auto-resize Guest Display
Instalando o WebGoat 5.4
1.Baixar o Webgoat 5.4
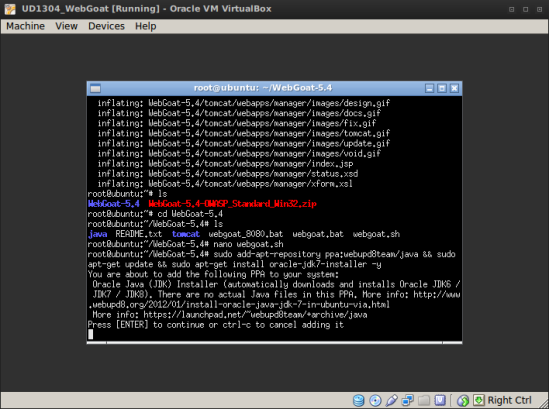
wget http://webgoat.googlecode.com/files/WebGoat-5.4-OWASP_Standard_Win32.zip
2.Descompactar WebGoat-5.4-OWASP_Standard_Win32.zip
unzip WebGoat-5.4-OWASP_Standard_Win32.zip
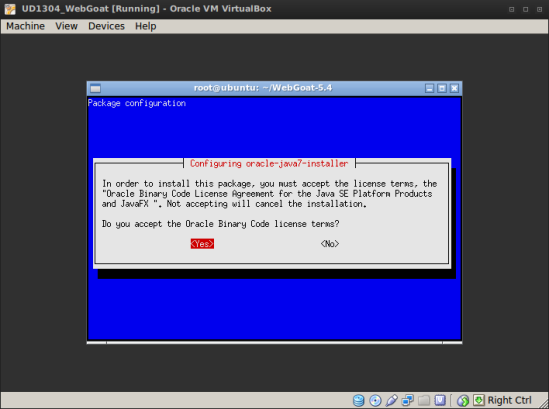
3.Instalar Oracle Java1.0.7 via ppa no Ubuntu 13.04
http://www.ubuntubrsc.com/instalando-oracle-java-7-ubuntu-ppa.html
sudo add-apt-repository ppa:webupd8team/java && sudo apt-get update && sudo apt-get install oracle-jdk7-installer -y
4. Executando o webgoat.sh e localizando erro da versão do Java:
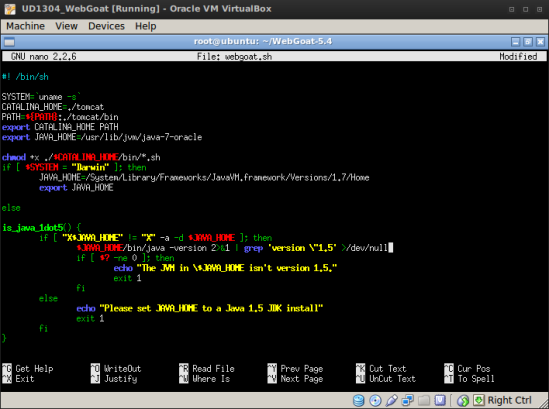
4. Verificando o arquivo webgoat.sh (original – versão para Sun Java 1.5):
nano webgoat.sh
# webgoat original
#! /bin/sh
SYSTEM=`uname -s`
CATALINA_HOME=./tomcat
PATH=${PATH}:./tomcat/bin
export CATALINA_HOME PATH
chmod +x ./$CATALINA_HOME/bin/*.sh
if [ $SYSTEM = “Darwin” ]; then
JAVA_HOME=/System/Library/Frameworks/JavaVM.framework/Versions/1.5/Home
export JAVA_HOME
else
is_java_1dot5() {
if [ “X$JAVA_HOME” != “X” -a -d $JAVA_HOME ]; then
$JAVA_HOME/bin/java -version 2>&1 | grep ‘version \”1.5’ >/dev/null
if [ $? -ne 0 ]; then
echo “The JVM in \$JAVA_HOME isn’t version 1.5.”
exit 1
fi
else
echo “Please set JAVA_HOME to a Java 1.5 JDK install”
exit 1
fi
}
is_java_1dot5
fi
case “$1” in
start80)
cp -f $CATALINA_HOME/conf/server_80.xml $CATALINA_HOME/conf/server.xml
$CATALINA_HOME/bin/startup.sh
printf “\n Open http://127.0.0.1/WebGoat/attack”
printf “\n Username: guest”
printf “\n Password: guest”
printf “\n Or try http://guest:guest@127.0.0.1/WebGoat/attack \n\n\r”
sleep 2
tail -f $CATALINA_HOME/logs/catalina.out
;;
start8080)
cp -f $CATALINA_HOME/conf/server_8080.xml $CATALINA_HOME/conf/server.xml
$CATALINA_HOME/bin/startup.sh
printf “\n Open http://127.0.0.1:8080/WebGoat/attack”
printf “\n Username: guest”
printf “\n Password: guest”
printf “\n Or try http://guest:guest@127.0.0.1:8080/WebGoat/attack \n\n\r”
sleep 2
tail -f $CATALINA_HOME/logs/catalina.out
;;
stop)
$CATALINA_HOME/bin/shutdown.sh
;;
*)
echo $”Usage: $prog {start8080|start80|stop}”
exit 1
;;
esac
========
4. Modificar o webgoat.sh para Oracle Java 1.0.7
Adicionar a linha e modificar 1.5 para 1.7:
export JAVA_HOME=/usr/lib/jvm/java-7-oracle
#! /bin/sh
SYSTEM=`uname -s`
CATALINA_HOME=./tomcat
PATH=${PATH}:./tomcat/bin
export CATALINA_HOME PATH
export JAVA_HOME=/usr/lib/jvm/java-7-oracle
chmod +x ./$CATALINA_HOME/bin/*.sh
if [ $SYSTEM = “Darwin” ]; then
JAVA_HOME=/System/Library/Frameworks/JavaVM.framework/Versions/1.5/Home
export JAVA_HOME
else
is_java_1dot5() {
if [ “X$JAVA_HOME” != “X” -a -d $JAVA_HOME ]; then
$JAVA_HOME/bin/java -version 2>&1 | grep ‘version \”1.7‘ >/dev/null
if [ $? -ne 0 ]; then
echo “The JVM in \$JAVA_HOME isn’t version 1.7.”
exit 1
fi
else
echo “Please set JAVA_HOME to a Java 1.7 JDK install”
exit 1
fi
}
is_java_1dot5
fi
case “$1” in
start80)
cp -f $CATALINA_HOME/conf/server_80.xml $CATALINA_HOME/conf/server.xml
$CATALINA_HOME/bin/startup.sh
printf “\n Open http://127.0.0.1/WebGoat/attack”
printf “\n Username: guest”
printf “\n Password: guest”
printf “\n Or try http://guest:guest@127.0.0.1/WebGoat/attack \n\n\r”
sleep 2
tail -f $CATALINA_HOME/logs/catalina.out
;;
start8080)
cp -f $CATALINA_HOME/conf/server_8080.xml $CATALINA_HOME/conf/server.xml
$CATALINA_HOME/bin/startup.sh
printf “\n Open http://127.0.0.1:8080/WebGoat/attack”
printf “\n Username: guest”
printf “\n Password: guest”
printf “\n Or try http://guest:guest@127.0.0.1:8080/WebGoat/attack \n\n\r”
sleep 2
tail -f $CATALINA_HOME/logs/catalina.out
;;
stop)
$CATALINA_HOME/bin/shutdown.sh
;;
*)
echo $”Usage: $prog {start8080|start80|stop}”
exit 1
;;
esac
5. sh webgoat.sh start8080
6. Abrir no firefox
7. Conectar-se a URL http://127.0.0.1:8080/WebGoat/attack e login e senha: guest
8. Pronto! WebGoat online.
Espero ter ajudado.
twitter
@firebitsbr
Ref:
http://webgoat.googlecode.com/files/WebGoat-5.4-OWASP_Standard_Win32.zip
http://www.ubuntubrsc.com/instalando-oracle-java-7-ubuntu-ppa.html
http://cdimage.ubuntu.com